Accept
What is two factor authentication, and why is it important?
Digital Estate Planning with Final Security is about protecting you and your loved ones from cybercrime, ensuring your important files are found and protecting your legacy. Get your free account and online will today; no credit card required.
Sign Up
Passwords are not secure enough
Passwords are everywhere! We are overloaded with passwords, whether we like it or not. As technology integrates itself into more areas of our lives, we are only going to add to our total number of passwords, which means more risk. With each password, you are increasing the likelihood of falling victim to a data breach. According to Wikipedia, It is estimated that in the first half of 2018 alone, about 4.5 billion records were exposed as a result of data breaches. In 2019, a collection of 2.7 billion identity records, consisting of 774 million unique email addresses and 21 million unique passwords were subject to breach.
Why are data breaches so common?
Technology is rapidly changing. Criminals have the advantage of being able to quickly adapt and exploit new vulnerabilities before organizations may even be aware they exist.
Information security was not always as important to companies as it is today. Companies would take shortcuts to save money and to get their product out to market as fast as possible, often to the detriment of the customer. These factors will always lead to trouble. In the same vein, information technology is a complex topic, and many companies do not have the resources to properly manage information and data security correctly. Even when a company is naive and not consciously making poor decisions that impact security, you still face risk as a customer.
As a user of technology, you must do everything in your power to help reduce the risk and likelihood of your accounts being compromised. This is especially important if your account contains sensitive data.
So, what is two factor authentication?
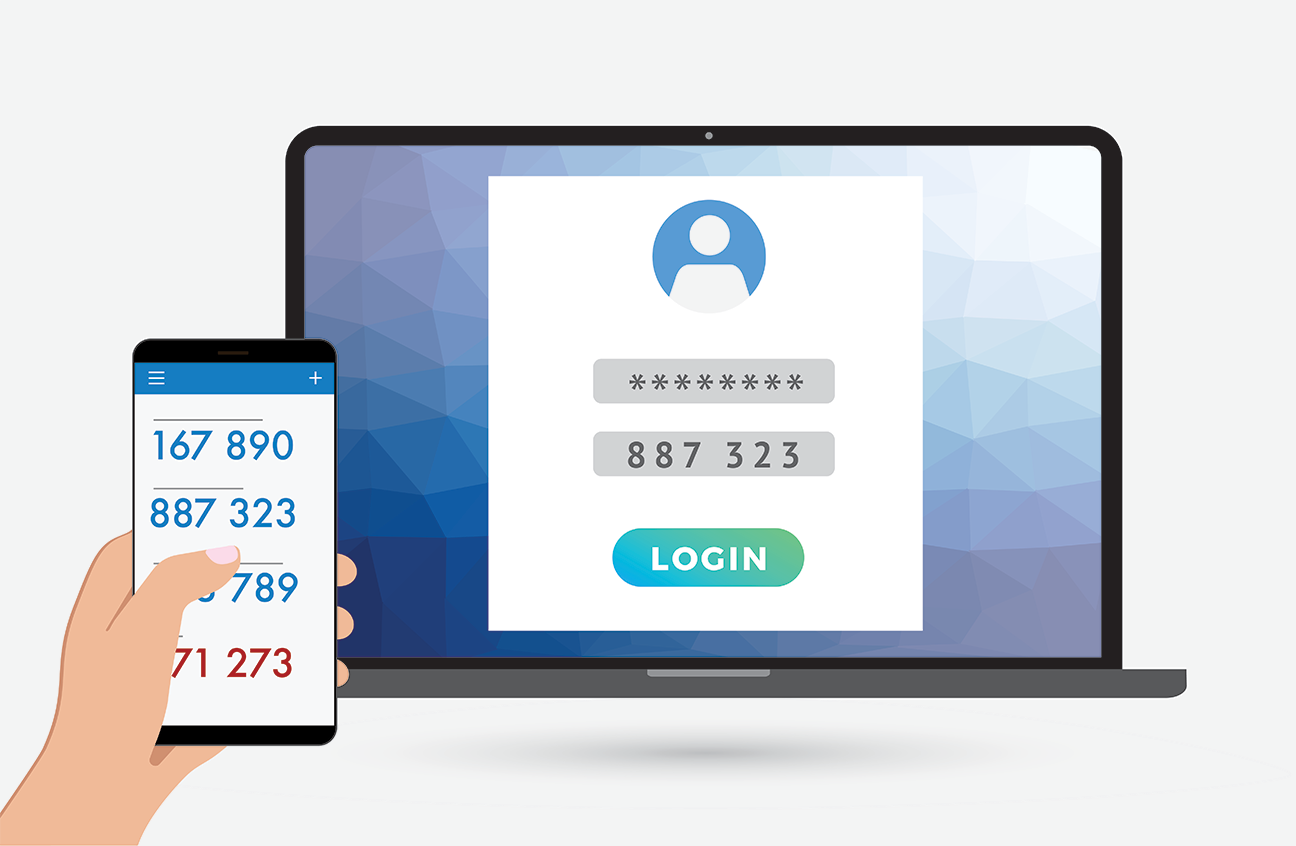
What is Two Factor Authentication
Two Factor Authentication is putting an extra layer, step or process before gaining access to your account. The process starts as any normal login would, where you must enter a password, but a second factor is also required - a passcode texted to you, a fingerprint, etc.
What are the most common types of two factor authentication?
SMS Text Messages
In this type of two factor authentication, you receive a special code via a text message. You would then take this code and enter it into the prompt on the websites, app, etc.
Voice / Phone Call Message
In the voice or phone call two factor authentication, you receive a phone call. In the phone call, you may receive a code to enter, like that of the text message above, or you could even be prompted to press a key to confirm.
Code from an app
This has become the most popular form of two factor authentication (authy, 2021). In this type of two factor authentication, you would install an app to your device. This app will then provide you with a unique code that refreshes every minute or so. To sync the app with the service, you will be provided with codes, or a QR code, that you can scan.
Why is Two Factor Authentication Important
We touched upon this above, but let's recap quickly.
Data Breaches
Data breaches have unfortunately become a common occurrence in our news today. ?According to Statista, which reports on the number of data breaches and records exposed in the United States since 2005, the number of cyber attacks is on an upward trend. In 2005, 157 data breaches were reported in the U.S., with 66.9 million records exposed. In 2014, 783 data breaches were reported, with at least 85.61 million total records exposed, representing an increase of nearly 500 percent from 2005. That number more than doubled in three years to 1,579 reported breaches in 2017? (Digital Guardian, 2018).
Rapidly changing technologies
We all know that technology changes rapidly. Thinking back to the 1990s, our smartphones have replaced many different types of devices: phones, cameras, video recorders, voice recorders, and so on. In Hosting Tribunal's article about how fast technology is changing, take a look at these telling stats:
- By 2025, 38.6 billion smart devices will be collecting, analyzing, and sharing data.
- The web hosting services market is to reach $77.8 billion in 2025.
- 70% of all tech spending is expected to go into cloud solutions.
- There are 1.35 million tech startups.
- The global AI market is expected to reach $89.8 billion.
- There are 4,383 million internet users.
- Solar energy adoption has grown by around 50%.
Companies awareness and approach to data security
Today, information security has become an important and growing part of our daily lives. The global cybersecurity market size is forecasted to grow to 248.26 billion U.S. dollars by 2023. Cybersecurity is the practice of protecting computer information systems, hardware, network, and data from cyberattacks (statista, 2021). This has not always been the case. Some companies out of a naive lack of awareness did not put the proper care into information security. Others companies, from market or investor pressure, have been forced to push products to market.
Take Our Privacy Crash Course
Learn more about How to Protect Yourself and Stay Safe Online From: Phishing, Identity Theft, Social Engineering, Hacking, Malware and Scams
Be aware of this Two Factor Authentication Issue
If you are using a two factor authentication app like Google Authenticator, you'll need to transfer your codes from your old device to your new one, or you could get locked out of your accounts! You can learn more about how to transfer your codes in this CNN article: New phone? Don't forget to transfer your Google Authenticator accounts.
Which account should I choose to enable two factor authentication?
You may not want to enable two factor authentication for all your accounts. While it does add the extra layer of security, it is an extra step. So, which accounts should you enable it on? Rule of thumb to enable it on would be any account where there is sensitive information or data. Credit card data, social security numbers, health records are some examples of data you would want to put the extra layer of security to protect. The good news is that many sites are now enforcing this by default.
Get started with two factor authentication today!
Hopefully we have convinced you of how important it is to ensure you've taken all possible steps to secure your accounts. Each service does things differently, but you'll likely find the options in the security settings under your account options. You can always Google the service and and two factor authentication if you are having trouble finding where it is located.
List of data breaches. (2021). From: https://en.wikipedia.org/wiki/List_of_data_breaches
What Is Two-Factor Authentication (2FA) - Authy (2021). From: https://authy.com/what-is-2fa/
The History of Data Breaches. (2018). From: https://digitalguardian.com/blog/history-data-breaches
How Fast Is Technology Growing - Moore's Law Can't Keep Up. (2020). From: https://hostingtribunal.com/blog/how-fast-is-technology-growing/
Global cybersecurity market forecast 2017-2023 | Statista. (2021). From: https://www.statista.com/statistics/595182/worldwide-security-as-a-service-market-size/#:~:text=The%20global%20cybersecurity%20market%20size,network%2C%20and%20data%20from%20cyberattacks.
Digital Estate Risk Assessment Calculator
According to AARP, it can take six months for financial institutions, credit-reporting bureaus and the Social Security Administration to receive, share or register death records. When you consider that timeframe and that cybercrime is now more profitable than the global illegal drug trade, your digital estate is the perfect target for criminals. We need to protect and organize our digital lives in preparation of our digital death.
How at Risk...
Is Your Digital Estate?
Get your free personalized digital estate planning report in just a few minutes.
Start Your Free Assessment
BANK-GRADE SECURITY
Your privacy, safety and security is our top priority and at the core of everything we do. Your data is encrypted and protected at every level. From typing on your computer, through the Internet and into our application and servers.
Learn more about how we secure your data.